In the last 20 years, the IT infrastructure has seen massive changes. With the introduction of the hybrid and multi-cloud environments, the IT department across industries has become very innovative. Modern networks are not bound by a clear perimeter with defined limits. Instead, the networks are complex, distributed, location-agnostic, and at times, vendor-agnostic.
These aspects make it highly accessible from any device or location. But, there is a downside to this flexibility. Since the network no longer has any set limits, cybercriminals can take advantage of this and easily get access by tricking users and systems.
This is when zero trust security comes on the scene. It assists businesses in protecting their data and assets. As the name suggests, it does not trust anyone with access to the system. Thus, preventing any kind of insider threats, including malicious threats and accidental damage.
In this article, I will introduce you to zero trust security, its core principles, steps to implement it by IT teams, some challenges to overcome for implementations, and others.
What Is Zero Trust Security?
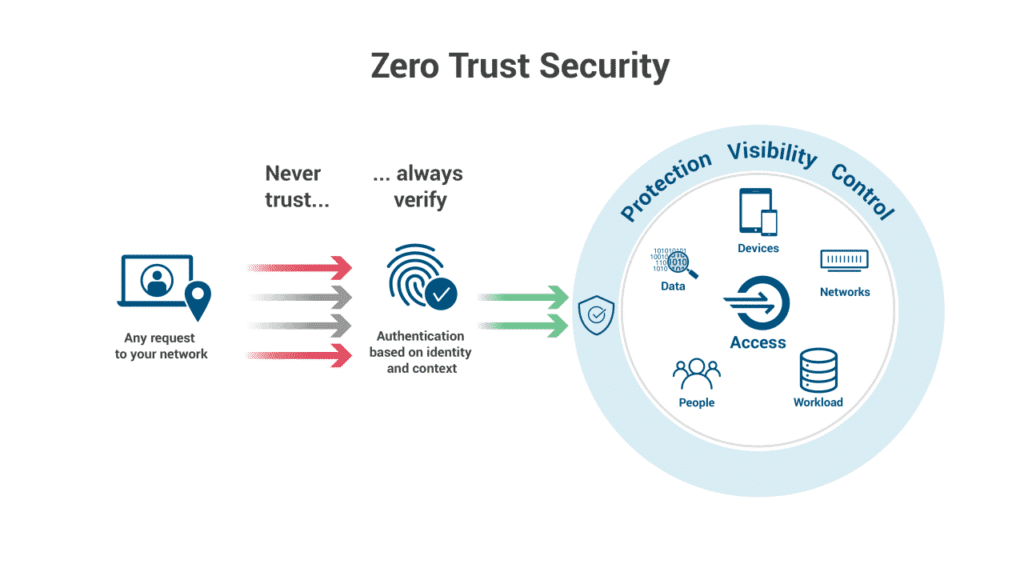
Introduced by Forrester analysts in 2010, the zero trust security model is based on the policy of not trusting anyone, even within the system, to get access to data and assets. It verifies the authenticity of the devices and users attempting to gain access to the network. The purpose of this model is to protect the network from within and prevent any insider threats. As a result, all the entities are treated to be suspicious, even if the user or device has been previously verified.
Before the introduction of zero trust security, organizations used the castle-and-moat methodology. This trusted everyone, users and devices, within the system, and allowed access to assets and network without strict verification methods. Though this traditional method was capable of protecting assets from any external threats, but had no means of detecting or eliminating internal threats.
Core Principles Of The Zero Trust Security Model
Re-Evaluate Default Accesses
The zero trust security model leaves no doubt, it trusts that threats can arise from both internal and external sources. No one, either inside or outside the network, is to be trusted. That’s why every access needs to be completely authenticated, authorized, and encrypted.
Multiple Protection Methods
Zero trust security deploys two types of preventative measures:
- Identity Protection & Device Discovery: It keeps track of which devices have what credentials, tracks network ecosystems, and sets up a normal behavior base. These help to build identity challenges and check for threats.
- Multi-Factor Authentication (MFA): Utilizes multiple methods to verify the authentication of the users. These methods include asking security questions, mail/ text verification, and logic-based exercises. MFA ensures that any user with access to a single verification method does not get access to the network.
Real-Time Monitoring
Real-time monitoring results in real-time threat discovery and quick response. By incorporating real-time monitoring, companies can detect, investigate, and respond to intruders quickly before they can spread across the entire network. Setting up real-time monitoring is a much better option than transferring events to a security information and event management solution (SIEM). Real-time detection of brute force attacks, credential spoofing, etc., will help to prevent them in time.
Part Of A Comprehensive Security Strategy
Zero trust security is not a comprehensive security strategy in itself. You need to combine it with other security technologies, like detection and response, endpoint protection, real-time monitoring, etc., to ensure end-to-end security of the network and assets.
Every organization has its unique requirements in terms of security. The chosen security measures must reflect the needs of the organization and network infrastructure. To achieve holistic protection, all security measures must compliment each other and work towards securing the network.
5-Step Method Of Implementing Zero Trust Security By IT Teams
The following 5-step method helps to develop and implement your zero trust security infrastructure. Your IT team can follow it to help build a trustworthy data loss prevention (DLP) and breach avoidance strategy:
1. Identify Threat Surface
IT environments are more dynamic today, and the old concept of threat surface is becoming irrelevant. Since most technical elements are not in the organization’s control, it is crucial to identify an attack surface. It means, focus on areas you must protect instead of getting overwhelmed by numerous policy implementations and tools deployment across the whole network.
The most risky areas of attacks can include,
- Confidential data that includes employee or customer information, and proprietary information that you must protect at all costs.
- Critical applications that have major roles in your most important business processes.
- Corporate services that support your organization’s daily work, from employees and executives to customer support teams.
- Physical assets such as IoTs (Internet of Things), PoS terminals, etc.
2. Map Network Flow
Check how traffic flows in the organization’s network. By this, you can also identify the system dependencies, like some systems will need access to databases that hold information about products, services, or customers.
Clearly define the flows that are required for operations. Others can either be mitigated or blocked.
3. Architecture Of A Zero Trust Policy
Zero trust policy is not a universal model, and it is developed around a specific protect surface. You can administer a microsegmentation and use it to create microperimeters surrounding important assets.
Primarily, you can start developing your architecture with a next-generation firewall (NGFW), which can be used for microsegmentation. Also, it is crucial to implement multi-factor authentication (MFA) at some point in your network for complete verification of users before granting access.
4. Develop A Zero Trust Policy
Once the zero trust architecture is complete, you can move on to design its policies. This can be done using the Kipling method or the 5 W’s method, in which the W’s stand for:
- Who is allowed access
- Via what application
- When should they be allowed access
- Where the asset’s location or address is
- Why do they need access, and how
The ZTN should ask these questions to every user, device, and network that asks for access.
5. Network Monitoring & Maintenance
Regular network monitoring can provide valuable information for network performance optimization and will also alert you in case of potential intrusion, quickly. To monitor the network, you must:
- Generate reports regularly that track network performance and display any abnormalities. Also, you can utilize these reports to check how ZTN affects your network and your employees, and improve it whenever necessary.
- Get analytics generated by your system, which can provide valuable insight into its functionality. These insights help to monitor network traffic, user behaviour, and performance of different components of the network.
- Get system-produced logs that display a time-stamped activity record. These records can either be checked manually or using analytical tools.
Challenges To Overcome When Implementing Zero Trust Security In Your Organization
To deploy zero trust security, you can face certain challenges on your way. I have listed some commonly faced obstacles that include complex infrastructures and others.
Complex Infrastructure
Many organizational infrastructures are composed of numerous servers, proxies, internal applications, SaaS, and databases. Some of which are on the cloud, and some are running on-premise. It is very difficult to meet the requirements of the cloud and on-premise environment, and also to secure each part of the network. All these factors can only add to the complexity of implementing a zero trust security.
Software Flexibility
To create and deploy a ZTN, you need a flexible software to run the system. In its absence, you might have to invest in unnecessary systems to protect all elements of the environment.
Cost & Resources
To implement ZTN, you need to invest significant resources, time, and financial support. To figure out network segmentation and who can access which areas of the network requires a lot of thinking and collaboration.
If you do not have a flexible system that integrates well with ZTN, you need to hire or allocate human resources that will incur substantial financial resources.
Once the zero trust security is put in place, you have a better chance of dodging security breaches and unauthorized access. As you might already have learned, ZTN is not an all-in-one security network. Instead, you must deploy other security measures to prevent both internal and external attacks on your organization’s data and assets.
Related: What Is DPaaS? Benefits, Features and Future of Data Protection
Related: AutoGPT: The Future of Autonomous AI Assistants








